
The Trojan Horse is a tale from the Trojan War about the false gift that the Greeks used to enter the city of Troy and win the war.
The Greeks built a huge wooden horse, and hid a select force of men inside. When the Greeks pretended to sail away, the Trojans pulled the horse into their city as a victory trophy. Then the Greeks waited…
When Troy was asleep, the Greeks crept out of the horse and opened the gates for the rest of the their army, which had quietly returned by ship. When Troy was at its most vulnerable and unsuspecting, the Greeks destroyed the city and won the war.
We have all heard the term “Trojan Horse” used metaphorically. One of the most fitting applications of this metaphor is when a malicious computer program is unwittingly run or downloaded by a user. Such programs are known as Trojan horses.
The Perfect (Cyber) Storm
Cyber security and hacking are on the rise and this effects all businesses, even those who don’t yet realise it. There is a perfect storm coming. If you think about it, there are more people online than ever before, there is more data produced daily than ever before, businesses are moving online at a rapid rate, we are in the midst of an API economy, there are directives such as PSD2, which are forcing banks to ensure all information is accessible in a readable common format (common API structures) and concurrently hackers and cyber criminals are on the rise and getting smarter and more efficient daily. Just as artificial intelligence (AI) will help humans become more efficient in the future, it will also make cyber criminals more efficient and alas more effective than ever before.
The main thing we can do to prevent it is be aware of some of the scams and protect ourselves accordingly.

Think for a second how sophisticated physical security has become. If you were a bank robber, think of the dangers of robbing a bank. The planning, the preparation, the get away driver, the risk of killing someone or yourself being killed!
Now, think of the “remote working’ option of working from home for any worker, why couldn’t a bank robber do this in today’s world? Think of putting all one’s effort into cyber crime or virtual bank robbery, now that is much more appealing than all the risk and hassle of physical bank robbery. In addition, consider how so few people are prepared for this, everything is shifting to a digital world. To use the Wayne Gretzky quote cyber criminals are “skating to where the puck is going, not where it is (today)”.
Phishing

Phishing refers to the process of “fishing” for sensitive user information such as credit cards, usernames and passwords, but even personal information such as mobile phone number.
Phishing scams are varied. Spear phishing is targeted at a specific individual, just as with content personalisation, phishing personalisation leads to greater success.
Clone phishing, as the name suggests, is when an original, previously delivered, email containing an attachment or link has had its content and recipient address used to create a cloned email. The attachment or link within the original email is then replaced with a malicious file or link and resent from a spoofed or fake email address. This technique exploits the social trust associated with the original sender and suggests the new email is just an updated version of the previously sent one.
The most interesting one I have heard of (and we discuss on this week’s Innovation show) is called “Whale Phishing”. As the name suggests, the cyber attacker is looking to catch a big fish. These attacks are targeted at senior executives.
Next, let’s see how Whale Phishing plays out, these scams occur very frequently and are often successful.
Inside Man (For those who have seen the movie, you will get this)

A malicious piece of software (malware) infiltrates a company’s email system via one of the methods above. Then the attackers play a patient waiting game (up to 200 days as we discuss on this week’s Innovation Show). The malware works its way up the email chain to create an org chart of sorts. The criminals establish who is the CEO, who is the CFO for example. They phish their mobile phone numbers from their email signatures or emails where they may have sent them or indeed from social media. Then, they phish and establish when the board meeting is on.
During the board meeting a text message is faked from CEO to CFO, it says to deposit a large sum to a stated account and not to ask any questions. In a huge number of cases the CFO follows orders and deposits the large sum. Game Over, funds lost. insurance premium increases.
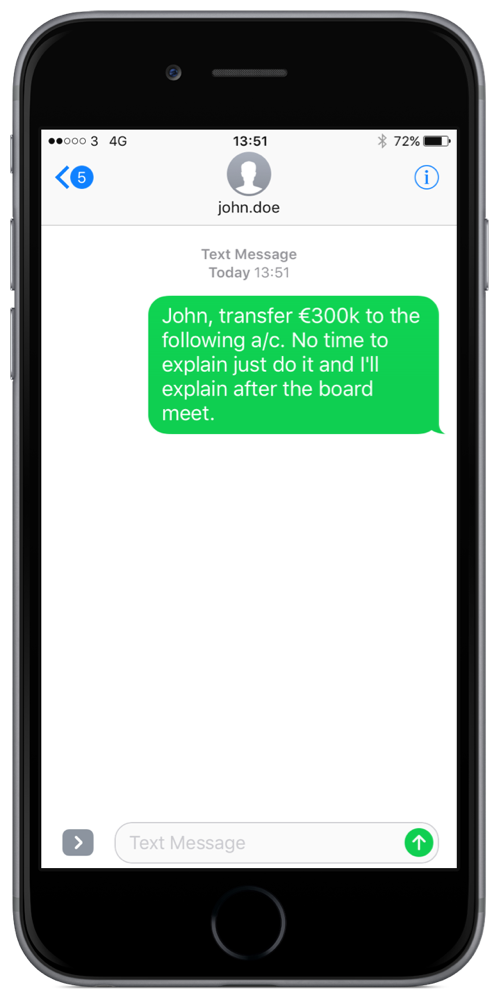
Smishing
“Smishing” is SMS Phishing, this is what we referred to above where the CEO and CFO’s numbers have been phished and then used to request funds. Smishing uses phone text messages to deliver the bait to induce people to divulge their personal information. This technique can be used in a huge variety of ways.
Social Media Phishing
So many of us have uploaded large amounts of ourselves to social media platforms, including our personal data, our photos and our location. It would be quite easy to piece a personal profile together, Fishing through someones bins for some old card statements could provide a missing piece to the puzzle. This information is often sold on the Dark Web.
But why do we get fake people on social media? Fake connections on Linkedin and fake profiles on twitter?
A while back, I recall a few people who I already know and had connected with requesting to connect again after we were already connected. I said it to one guy, he said that a few people had mentioned this to him. Then I had a few requests after that, where I looked at who the person was, were they real, did they have many connections already and did we have shared connections.
To my surprise I received at least one of these per week. But Why?
If I have my contact details on a social media site an accepted connection can access them, so for any of my connections I can see their email address and mobile number if they have uploaded them.
As a cyber criminal I can access that number, send a fake text and then track your keypad, this can give them access to passwords and account numbers.
One scam I received, but didn’t take the bait was that someone had an amazing opportunity for me and all I had to do was share my number and they would call me. I said no thanks and they insisted before eventually going away. If I had shared my number I might have been a victim of a missed call scam, whereby I miss a call (it rings just once), I call back and it is a high premium number $50 per minute for example. This can happen with texts also.
Oftentimes one might receive an email from a trusted profession like an army officer, a doctor or even a Nigerian Prince. Below is one I got the other day from a high ranking army officer General Carter F. Ham (good name).
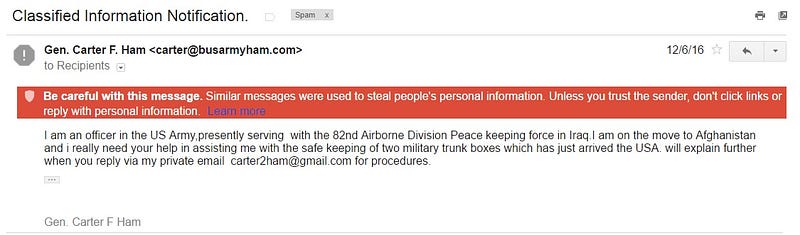
Beware of Greeks (Nigerian Princes) bearing gifts
I have received so many amusing hoax emails claiming that I have won an inheritance from a distant hitherto unknown relative who has left me his crown jewels. The variants are Princes, Senators and indeed Army Officers as per above. I have always scoffed at these, but realise that there are many people of different generations, who are simply unaware of how these scams can work.
It only takes one to get past the security measures and everyone is at risk. Once there is poison in the well, everyone can be poisoned.
Solutions
The main thing we all can do is be aware and have senior leadership buy-in. IT policies and education goes a long way as so many of us are simply oblivious to the threat. Simple things like putting passwords on sensitive document files and texting the number. Simple things like having a policy at home that kids tell the most tech savvy parent about dodgy emails they may receive.
For many more examples of scams and some more hot tips, check out this week’s innovation show. We talk to Ronan Murphy, CEO and founder of Smarttech, he tells us of some of the latest scams and raises our awareness of how to prevent being a victim. Pat Moran is PwC Head of Cybercrime & IT Forensics, he gives us some astonishing stats on cybercrime and gives us some practical, but excellent advice on how to prevent being a victim in work or even at home.
Michael O’Dwyer has a fantastic story to tell of how he has built a company using personal drive and government funding. He tells us about his company SwiftComply and gives some great advice for startups.
Finally, ex-Army officer and telecoms man Fintan McGovern tells us how he and the Firmwave team are rolling out a different network and conquering the business world. We talk cyborg chickens and connected bus shelters.
For now I leave you with what would have happened if Hitler was a victim of a Nigerian email scam…